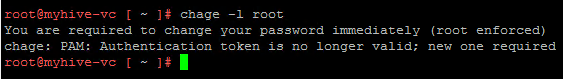
As a best practice, we should keep all the server patch with latest update. This tutorial tells i will demonstrate how to patch your Debian server with the latest updates. You need to use either apt-get command or apt command to apply patches to Debian Linux server.
Step:
i. Connect to your Debian system via SSH. Once you are in the terminal, enter the following commands:-
apt-get update
apt-get update command is used to download package information from all configured sources